
This page aims to provide research and resources for navigating digital defense strategies, designed to be used by people of all ages and abilities. It includes an array of glossaries for different levels of tech literacy among users, as well as a cache of useful resources from organizations, research and advocacy groups, and academics.
The main component of this page is a collection of maps designed to help users evaluate their specific needs based on access and device type.
For instance, tools that would be helpful for someone who can only reliably use a shared computer at their public library or school (many young people) would be different than the tools useful for someone who has administrative privileges on a new laptop.
There are sections of guidance for digital defense on phones, computers, and shared devices as well as a section outlining strategies applicable for anyone on any web-enabled device. The maps cover browsers, add-ons, apps and toggling settings local to a device among other suggestions.

I am hopeful that by using visual aids that break down the vast topic of digital defense, the strategies presented will be less overwhelming for people; the map’s “if X, then Y” structure of mapping out strategies has been fundamental in my own positioning within the digital defense ranks.

OUR DATA OUR BODIES: COMMONLY USED TERMS
Readability: 5/5, Intersectional & Anti-Racist Language: 5/5, Technical Explanations: 3/5
Good for teaching and having a wider purview of the communities and systems that are affected by data exploitation.
Readability: 5/5, Comprehensive Explanation of Terms: 5/5 (has notes on word definitions within definitions), Technical Explanations: 5/5
This, in tandem with the Our Data Our Bodies glossary, would be the perfect pairing of technical and culturally self-aware reference resources.
Readability: 2/5, Range of Terms: 5/5
Hard to read; however, this is useful like casually flipping through an encyclopedia is useful
Readability: 2/5, Technical Jargon: 5/5
If you’re looking for textbook definitions pulled straight from a government cybersecurity lexicon, look no further.

Database of known police tech in the U.S. which lays out what the tech does and where it’s used.
Browser add-on via EFF that ensures secure website connections
THINKING ABOUT WHAT YOU NEED IN A SECURE MESSENGER
Article via EFF that lays out different security strategies for text-based communication
Comprehensive guide to digital self-defense strategies including passwords, encryption and communications. Includes curated strategies for specific scenarios (LGBTQ youth? Attending a protest?Journalist on the move?)
Online tool that allows you to see what information about you/your location is visible from your browser
HOW TO OPT OUT/SUPPRESS PERSONAL INFORMATION ON PEOPLE-SEARCH SITES
Non-exhaustive guide on how to conduct information suppression requests for most public people-finder sites (Whitepages, Spokeo, etc.)
DIGITAL DEFENSE STRATEGY MAPS
(CORRESPONDING MAP LINKS ARE FOUND AT BOTTOM OF PAGE)
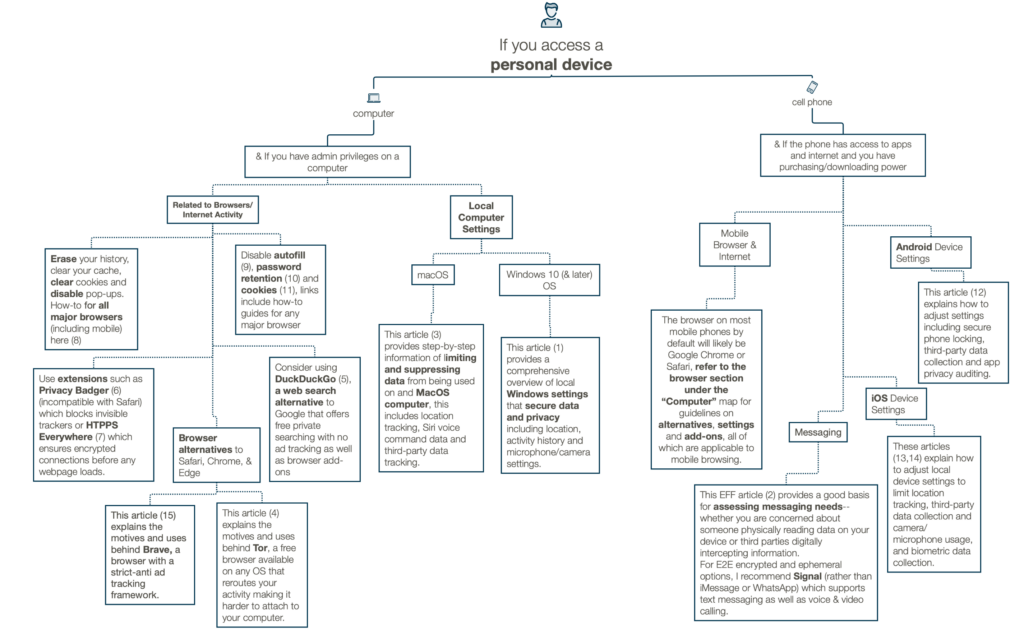


Corresponding Links to Personal Device & Shared Device maps
- Windows 10 Privacy Settings
- What You Need in A Secure Messenger
- MacOS Privacy Settings
- Tor Browser Explained
- DuckDuckGo
- Privacy Badger
- HTTPS Everywhere
- How Do I Clear My Web Browser?
- How To Disable Autofill
- Disable Browser Password Managers
- General Privacy Settings Guide
- Android Privacy Settings Guide
- iPhone Privacy Settings Guide
- iOS 15 Privacy Settings Guide
- About Brave Browser
- Superlogout
- Clearing History in Any Browser
- Clearing Cookies
- 2 Factor Authentication and How To Set it Up
- Proton Mail/About
- Encrypted Cloud Storage
- Secure Note Taking Apps
- LastPass


